About identification management
Effective identification management helps organisations to reduce and/or prevent fraud, loss of privacy and identity theft by applying good practice processes.
What is identification management?
Managing the processes of:
- verifying information
- connecting it to Entities, including people
- connecting these to reusable Authenticators.
It applies at the enrolment of the Entity and throughout the lifetime of their relationship with an organisation, whether online, in person or over the phone.
The identification management approach acknowledges the difference between the Entity in the real world, person or non-person, and the digital representation of them in a system.
Why is it important?
Effective identification management helps to reduce the impacts of identity theft. Which can result in fraud, loss of privacy and security, and have a detrimental effect on both an organisation and its customers.
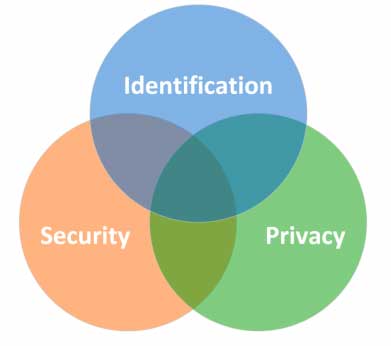
Good identification management practices contribute to effective decision-making and mitigation of risks. Identification works with privacy and security to protect information assets.
The identification management elements
Multiple elements are needed in identification management to achieve the desired outcomes for Entities, such as people. The diagram below depicts how these elements work together.

Detailed description of the image
An Entity (for example, a person) wants to get a Credential that they can use to get a service from a Relying Party (for example, an organisation). The Entity goes to a Credential Provider to get an applicable Credential and then either presents their Credential directly to the Relying Party or the Credential Provider presents it to the Relying Party for them, sometimes via a third party.
Descriptions of the elements and their relationships
These elements and the wider language around them make understanding the field of identification management complex. To help simplify things a list of identification terminology and how it is used has been developed.
Support for identification management
To support the field of identification management four technical standards have been published along with a range of guidance.
Training courses and drop-in clinics are available to aid in the development of capability in this field.
The Identification Management Team at Te Tari Taiwhenua Department of Internal Affairs provide independent advice and guidance.
Contact the Identification Management Team
Identification management and other practices
Identity management
Identity and identity management tend to focus on minimal attributes and their management rather than wider business needs, and the processes and human behaviours essential to prevent identity theft and the impacts of this. Therefore, the material on this site takes a different and broader approach to guide best practice and the effective development of solutions.
Digital identity
Digital identity is a term used for several concepts including electronic credentials, digital enrolment and social footprint.
It can also mean the application of identity management or identification management in the digital channel, digital identification. In New Zealand, the Digital Identity Services Trust Framework is developing a system of accredited digital providers.
Trust framework for digital identity
Privacy and security
Identification management is a practice that is separate from but closely related to Privacy and Security. While several requirements within the Identification Standards contribute to information privacy and security, they do not replace the need to apply relevant standards within these separate practices.
Detailed description of the image
Utility links and page information
Last updated

